Understanding Use-After-Free (UAF)
Introduction
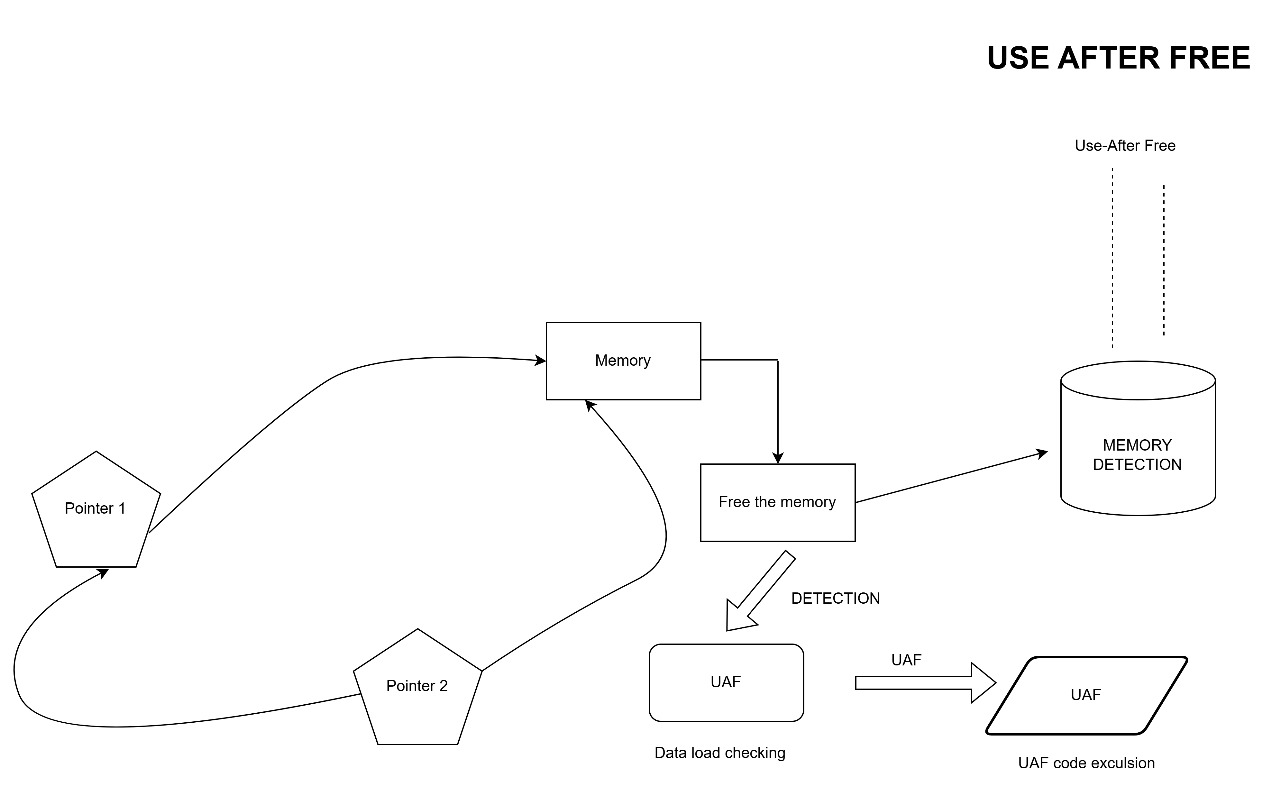
The Use-After-Free (UAF) vulnerability is a critical flaw in memory management that occurs when a program accesses memory after it has been deallocated. In the Linux kernel, where dynamic memory allocation is integral, UAF can lead to severe consequences such as:
- Memory corruption
- System crashes
- Privilege escalation
- Arbitrary code execution
This vulnerability stems from improper memory management practices, including dangling pointers, premature deallocation, race conditions, and incorrect reference counting.
Understanding the Problem
Memory Management in the Linux Kernel
The Linux kernel frequently allocates and frees memory using allocators such as kmalloc, vmalloc, and kfree. Kernel subsystems like device drivers, networking modules, and file systems are particularly vulnerable due to their complex memory management requirements.
Vulnerable Areas
- Networking Modules: Mismanagement of network buffers (e.g.,
sk_buff) can trigger UAF. - File Systems: Mishandling inodes can lead to UAF conditions.
- Process Management: Bugs during task structure cleanup may cause memory to be accessed post-deallocation.
How Exploits Occur
Attackers exploit UAF vulnerabilities using techniques like:
- Heap Spraying: Filling memory with predictable data to overwrite freed memory.
- Arbitrary Code Execution: Injecting malicious payloads into freed memory blocks.
- Privilege Escalation: Gaining unauthorized kernel-level access by manipulating freed memory.
Visual Representation: